Introduction
Geospatial intelligence (GEOINT) refers to intelligence gathered from analysing imagery and geographical information. This definition applies to both the analytical process and end-products. Technological advancements have provided governments with advanced analytical tools required to conduct increasingly precise analysis that bolsters national security. Today, the demand for information sees sensors collecting copious data in diverse environments. This information offers insight into issues from strategic route selection to analysing an adversary’s intentions.
This article explores GEOINT’s techniques and technologies through three case studies chosen to showcase its breadth of applications. GEOINT’s attributes will be highlighted to demonstrate its potential for strategic leverage and supporting different situations. GEOINT’s defence uses can divided into two broad categories:
- Terrain and spatial analysis – Involving route selection, line-of-sight, and threat capability analysis.
- Descriptive and anticipatory analysis – Determining what an adversary is doing and what they intend to do.
Finding Osama Bin Laden: Analytical tools for target acquisition
GEOINT played a significant role in locating and killing Osama Bin Laden. Long-term, human terrain mapping fuelled by anthropological analysis assisted in developing probabilities concerning Bin Laden’s location (Cozine, 2013; Matthews 2011; Albro, 2010). Satellite imagery was scrutinised for indicators of Bin Laden’s presence (Panetta & Bash, 2016). GEOINT contrasted other intelligence, like layering GEOINT over signals intelligence (SIGINT), to enhance situational understanding of otherwise irrational human behaviours (Cozine 2016).
Image science and modelling produced an accurate 3D model of Bin Laden’s compound used for the planning the kinetic action (Cozine, 2013; Matthews 2011). Although SIGINT facilitated depicting courier networks (Deniston, 2011), Human Intelligence (HUMINT) led to the interrogation of key Al Qaeda agents (Dahl, 2014). Fusing data between collection mediums allowed for layered analysis to bolster or refute assumptions (Prunckun, 2019).

Figure 1: 3D ‘Mud-model’ of Bin Laden’s compound (ABC News, 2014).
Correctly distinguishing between normal and abnormal was pivotal. The compound’s fortification and lack of electronic signatures (Cozine, 2013) were deemed abnormal. A positive indicator was inhabitants burning rubbish, hypothesised as concealing counter-intelligence opportunities (Prunckun, 2019; Deniston, 2011; Cozine, 2013).
GEOINT facilitated approaching data objectively and from multiple perspectives. Fusing data helped concentrate or generate new assumptions. Upon designating the compound as an ‘Area of Interest’, satellite imagery was scrutinised to support or deny the assessment of Bin Laden’s presence. Aspects like construction, size, electronic signature, and human terrain were contrasted in ‘finding absence of normal, and presence of abnormal’. The imagery depicted heightened walls, blackened windows, and peculiar behaviour.
Lindt café siege: The value of spatial analysis in tactical response
This case study demonstrates the tangible impact when GEOINT is omitted from operational planning, highlighting specific ways this contributed to unfavourable outcomes. The intent is to identify situation-specific problems and retrospectively show how common geospatial tools could have helped mitigate these issues.
In 2014, a lone gunman took hostages inside the Lindt Café in Sydney. A 16-hour standoff ensued before police stormed the café, resulting in two hostage deaths, along with the gunman. In the aftermath, significant controversy arose regarding why the police snipers never took lethal action against the gunman (Taylor, 2019). A key factor was the lack of geospatial analysis to inform sniper positioning and engagement options.
The sniper teams chose their positions based on limited first-person observations (New South Wales Government [NSWG], 2017). Albeit a common practice, (Department of Defence, 2017) as illuminated during the inquest, these improvised positions restricted the snipers’ fields of fire and ability to cover potential targets (NSWG, 2017). Proper geospatial analysis, both prior to and during the siege, could have enabled more strategic sniper deployment.
The broader lesson is that inadequate integration of geospatial intelligence tools directly contributed to suboptimal positioning, limited engagement opportunities, wasted time, and ultimately failure to resolve the incident without loss of innocent life. As illustrated by this case, the real-world consequences of not leveraging geospatial analysis to inform tactical decision-making can be severe. The takeaway is the vital role GEOINT plays in support of complex contingencies across the spectrum of operations.
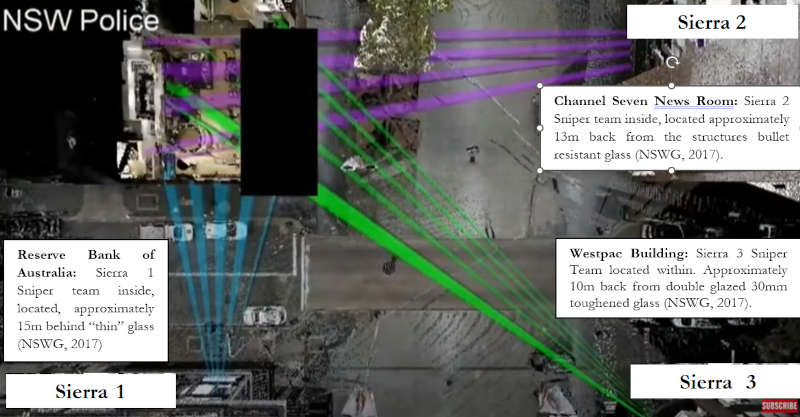
Figure 2: Geographical information system (GIS) snapshot of static sniper triangularisation upon the Lindt Café. (Nine News, 2019).
h4p>South China Sea: Descriptive and anticipatory analysis
This example demonstrates descriptive and anticipatory GEOINT analysis providing insight on adversary intentions. In the South China Sea (SCS), data collection relies heavily on satellite-mounted sensors due to strategic constraints.
Since the 19th century, China has exhibited expansionist intentions (Buszynski, & Roberts, 2014), increasingly detectable with island construction coinciding with satellite technology developments. In 2014, Digital Globe, a commercial company specialising in geospatial content and imagery, gained permission from the U.S. Department of Commerce to sell high-resolution SCS imagery from 30cm resolution satellites (Digital Globe, 2014, Carlson, 2018).
While considered international waters, the SCS’s location has caused contention from overlapping sovereignty claims (Global Conflict Tracker [GCT], 2019). Digital Globe imagery depicts China asserting dominion by building military facilities on reefs (Asia Maritime Transparency Initiative [AMTI], 2020, GCT, 2019).

Figure 3: Satellite timeline imagery of Subi Reef undergoing Chinese development. Location: 10° 55' 25" N 114° 5' 5" E (approximately 290 Nautical miles WSW of Vietnam’s coast). Image sourced: (AMTI, 2020)
The Asia Maritime Transparency Initiative (AMTI) uses Digital Globe data to generate substantial ‘time-lined’ imagery and analysis (Figure 3). Combining imagery, technical analysis, and experts has brought stakeholders to the conclusion that China aims to extend its Exclusive Economic Zone with the islands (see figure 4). As China militarises the region, satellite imagery becomes critical for timely, accurate anticipatory intelligence on intentions holding national defence implications.

Figure 4: Assessed to be a Chinese radar facility on Subi Reef. Image source: (AMTI, 2020)
Conclusion
It is difficult to fully articulate certain intuitive aspects of GEOINT analytical practices. Many techniques exist only inside the subconscious minds of experienced analysts, forming an analytical framework that guides their thinking (Prunckun, 2019). However, the examples in this article provide an appreciation for GEOINT’s broad strategic potential and unique conveyance of information through images rather than words.
This visual and spatial dimension distinguishes GEOINT from other intelligence disciplines and echoes its unique worth. In time-critical, information-heavy environments burdened by an excess of data, GEOINT’s ability to convey insights “at a glance” offers clear strategic advantages. By combining advanced technologies for data collection with specialised human analytical tradecraft, GEOINT enables both detailed tactical support and high-level anticipatory intelligence that is difficult to achieve through other means. The case studies illustrate only a fraction of GEOINT’s expanding role in diverse defence applications, from hunting key targets to monitoring regional flashpoints.









