This article was endorsed by the SMEs at 7th Signal Regiment
This article was endorsed by the SMEs at 7th Signal RegimentIntroduction
Electronic Attacks have become a crucial component of modern warfare. Targeting enemy communications, radar, and navigations systems significantly impair their ability to coordinate and execute operations, rendering them combat ineffective. So how does an electronic attack work? This article provides an overview and examples of electronic attack to help you identify and mitigate the risk of you falling victim to such an attack.
The Australian Army relies on voice and data communications for the effective command and control (C2) of its force elements. From conducting an assault over an enemy position to extracting wounded personnel, the Combat net radio (CNR) is an essential capability in warfare that is often taken for granted.
However, as history has demonstrated, an over-reliance on any tactic or capability presents an opportunity for exploitation. Every war fighter will be required to communicate over the in-service radio at some point. It is therefore critical that every user understands their role in electronic protection (EP), has a basic understanding of electronic warfare (EW), and can respond appropriately to Electronic Attack (EA).
EA can degrade and deny CNR. Ukraine has provided us with tangible insights into how contemporary EA is employed and the effects it can have. Australian soldiers must be armed with the knowledge of what EA is and how they can best mitigate it, to fight through and win.
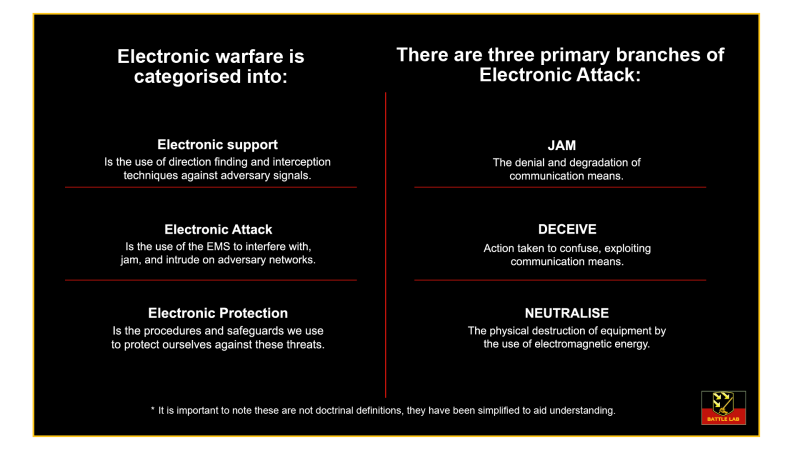
| What you need to know about EA: The aim of EA is to prevent or reduce an enemy’s effective use of the EMS through the use of electromagnetic energy. Priority of effort is usually given to disrupting C2, fire control, and intelligence communications systems. |
Jamming
Defined as the deliberate radiation, re-radiation, or reflection of electromagnetic energy with the objective being to prevent or reduce the use of electromagnetic devices or systems by the enemy. Typically, jamming is employed in one of three ways: Spot; Barrage; Sweep.
Jamming can be employed in a constant or reactive mode. In constant mode, the jamming signal constantly emits energy, regardless of transmission detection. In a reactive mode, the jammer waits on a given frequency and emits for the duration of a transmission before switching to ‘standby’. You could liken reactive mode to the fire control order “WATCH AND SHOOT”.
Examples of Jamming
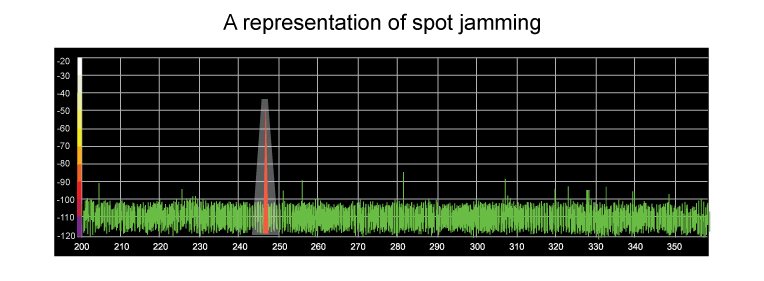
Spot jamming occurs when one channel or frequency is jammed at a time, concentrating all of the power from the jammer onto a given frequency.
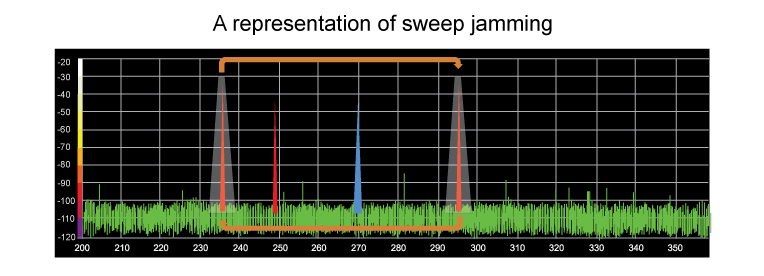
Sweep jamming is when a set of frequencies is targeted. Jamming moves through the given range sequentially but only targets one frequency at a time, similar to SPOT. The jamming signal can move freely within a given range, excluding frequencies as requested by the operator.
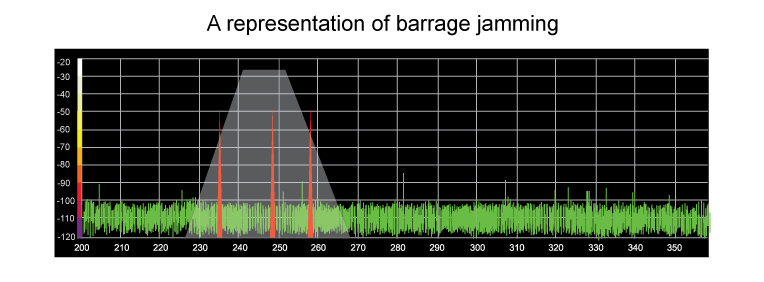
Barrage jamming is very similar to a fixed jam, whereby a broad band of frequencies is simultaneously jammed. Due to the requirement to ‘spike’ power across multiple frequencies it is easier to work through and may have a degrading rather than a denial effect.
Conclusion
Electronic attacks have become a crucial component of modern warfare. These attacks involve jamming, hacking, and the use of electronic pulses to disrupt or disable electronic networks on the battlefield. Electronic attacks can create opportunities for gaining a strategic advantage and can significantly impact the outcome of a conflict. The increasingly heavy reliance on technology in warfare has made electronic attacks a key component of contemporary military strategy.